Counter-Strike Is Broken
NOTICE
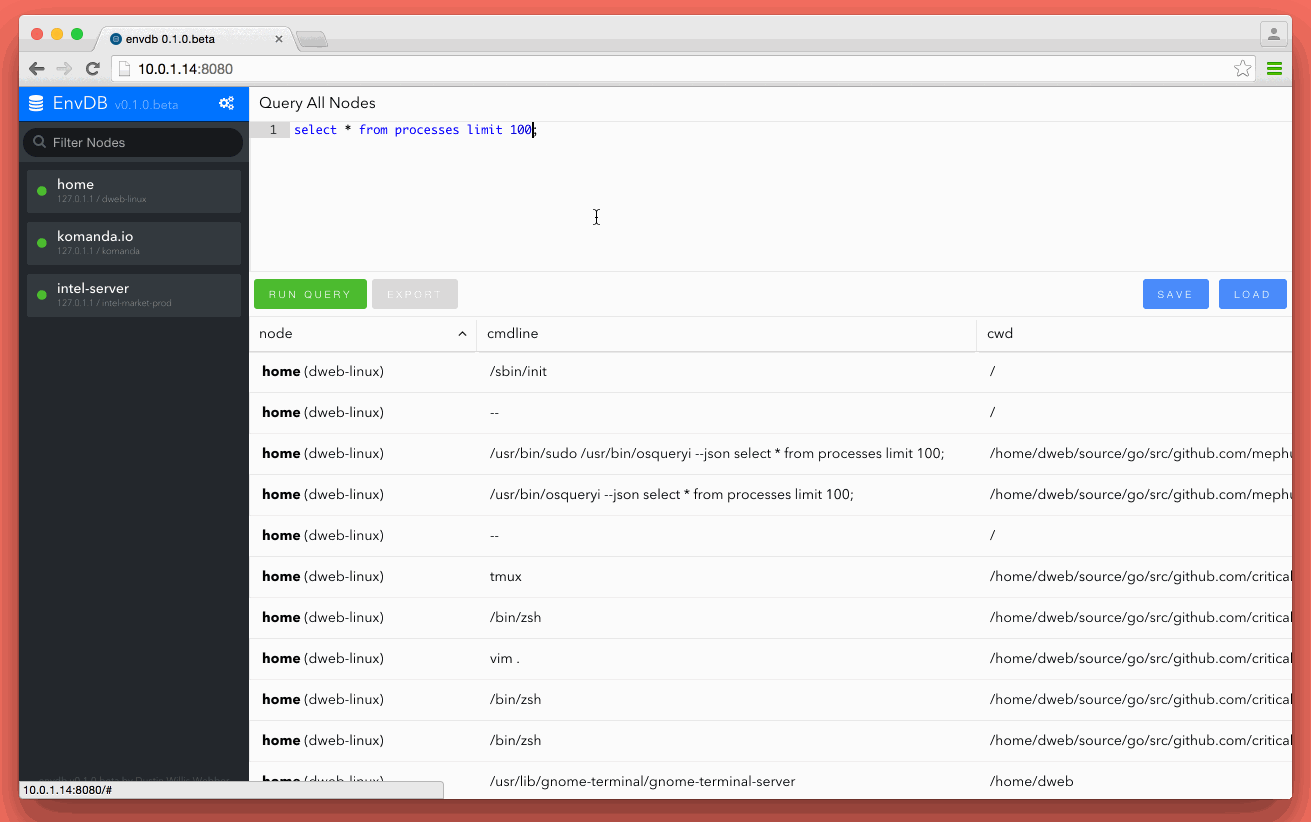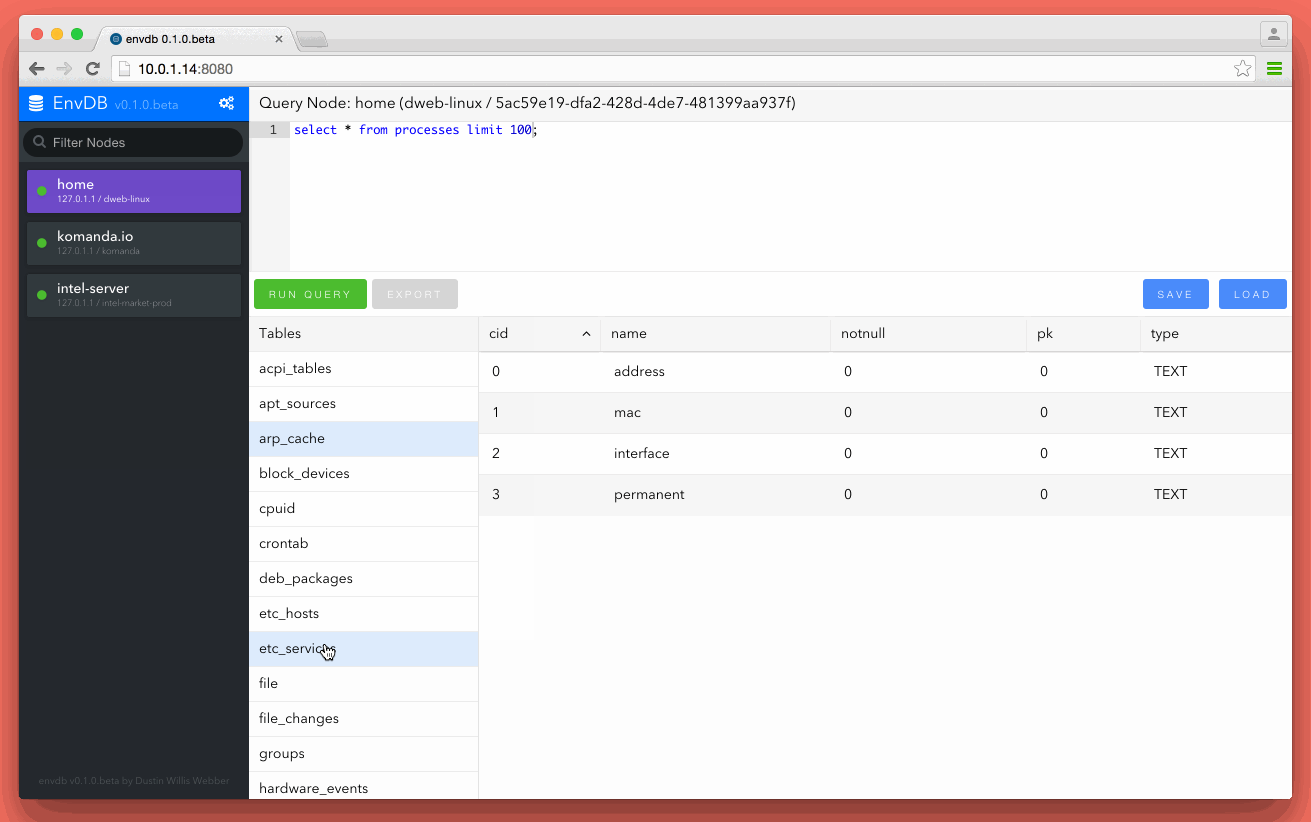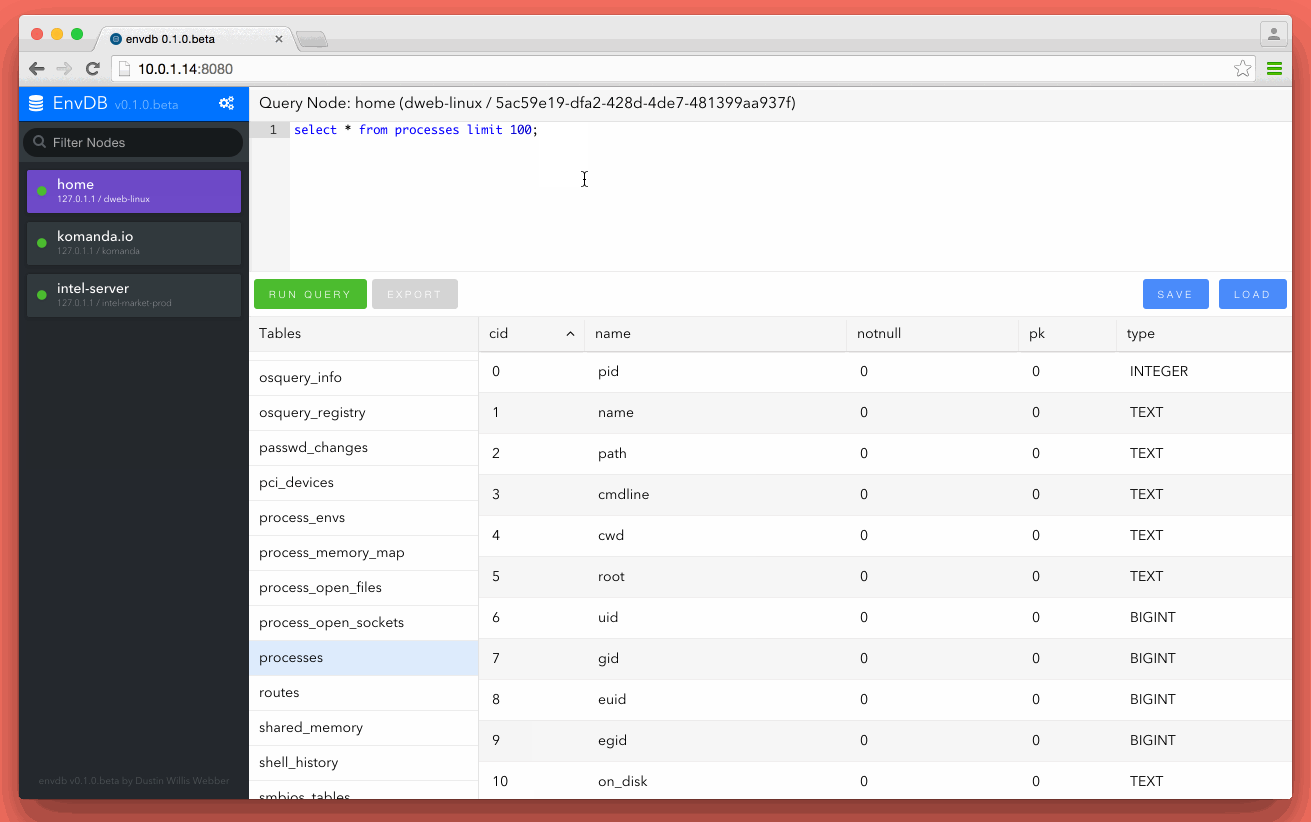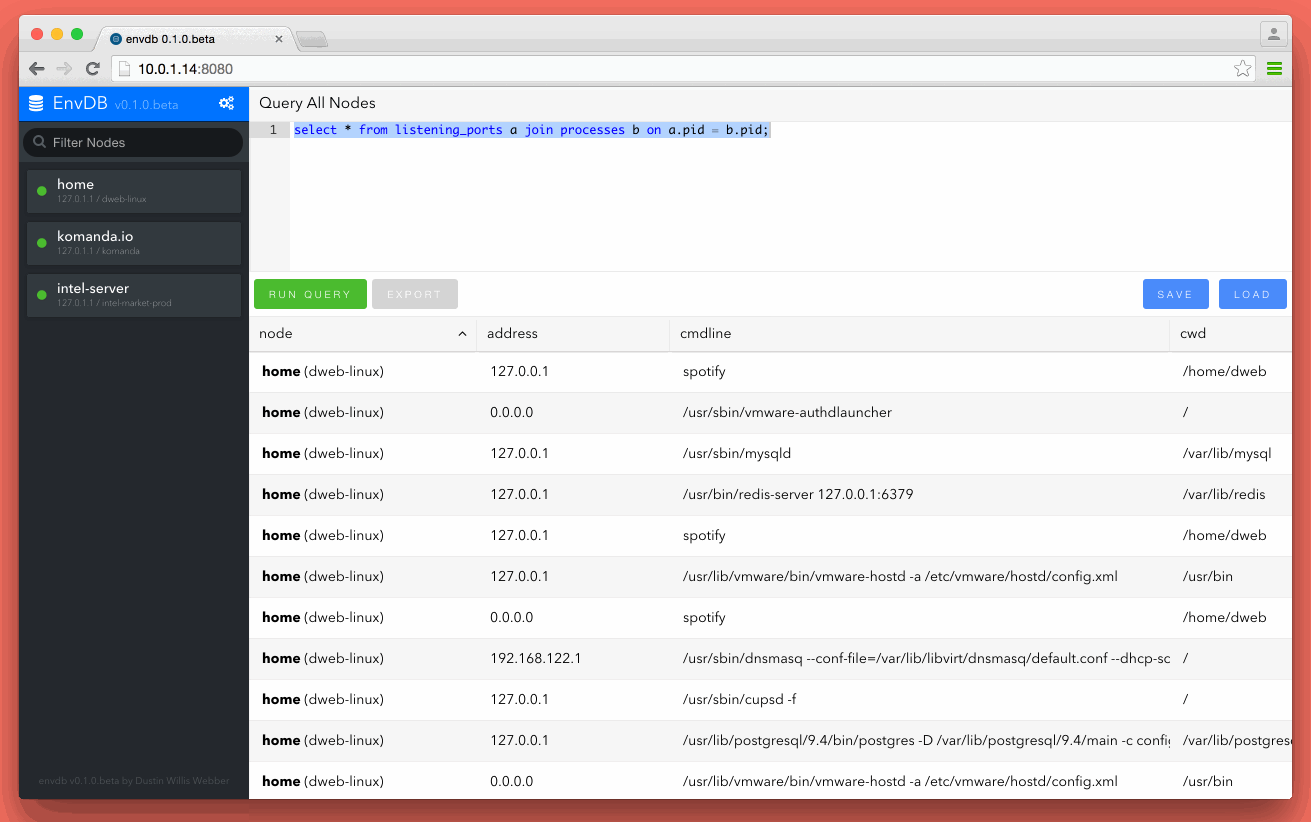
This blog post is about VAC signature detection. NOTHING else. A lot of people are having panic attacks about other technical features that this does not cover. Also, Assualt Cube is used as a demonstration with VAMemory which was the memory c class used while doing CS:GO research. My reason for posting is why easy, old and simple memory modification cheats using known memory modifications DLLs are not being detected after months of use. I have not and will not reverse Warden, VAC or care about other anti-cheat technics being used in them. I simply don’t care and it’s out of scope for this post.
TL;DR The Counter-Strike [VAC] anti-cheat engine is signature based (among common other things) and people selling cheats know this. They could flood the community with so many different signatures that Valve could never keep up with detection. They need to evolve by either monitoring...